一、现象描述
如图1所示,Switch为网关,Switch_1(框式交换机)经常脱管,且Switch_1下用户存在上网掉线,Ping网关存在时延、不通等现象,而Switch_2下联业务正常,Ping网关正常。
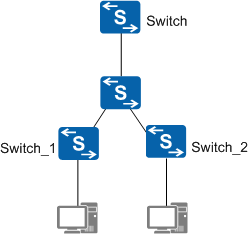
图1 交换机受到ARP报文攻击导致Ping不通组网图
二、原因分析
Switch_1上存在源MAC固定的ARP攻击导致用户无法进行正常ARP交互。
三、处理步骤
在Switch_1上执行以下操作:
3.1 查看设备CPU占用率,判断CPU占用率较高。
<Switch_1> display cpu-usage
CPU Usage Stat. Cycle: 10 (Second)
CPU Usage : 82% Max: 99%
CPU Usage Stat. Time : 2010-12-18 15:35:56
CPU utilization for five seconds: 68%: one minute: 60%: five minutes: 55%.
发现CPU占用率达到82%。
3.2 查看存在临时ARP表项,初步判断设备的ARP表项学习存在问题。
<Switch_1> display arp
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE VPN-INSTANCE INTERFACE
VLAN/CEVLAN
------------------------------------------------------------------------------------------------------
10.137.222.139 00e0-fc01-4422 I - Eth0/0/0
10.137.222.1 0025-9e36-e8c1 20 D-0 Eth0/0/0
10.137.222.100 0025-9e80-b278 6 D-0 Eth0/0/0
10.137.222.99 00e0-4c77-b0e1 9 D-0 Eth0/0/0
10.137.222.173 000f-3d80-cba4 18 D-0 Eth0/0/0
10.137.222.34 0025-9e36-e8c1 1 D-0 Eth0/0/0
10.137.222.172 0016-ec71-ea8c 7 D-0 Eth0/0/0
10.137.222.35 0025-9e36-e8c1 18 D-0 Eth0/0/0
10.137.222.179 0014-2ae2-3128 20 D-0 Eth0/0/0
10.137.222.38 0025-9e36-e8c1 17 D-0 Eth0/0/0
10.137.222.175 0014-2261-2b22 1 D-0 Eth0/0/0
10.1.1.3 Incomplete 1 D-0 GE5/0/0
500/-
10.1.1.2 Incomplete 1 D-0 GE5/0/0
500/-
172.31.255.255 00e0-fc01-4422 I - Vlanif6
10.0.0.139 00e0-fc01-4422 I - Vlanif10
172.16.0.4 00e0-fc01-4422 I - Vlanif192
20.1.1.1 00e0-fc01-4422 I - Vlanif200
192.168.2.2 00e0-fc01-4422 I - Vlanif100
------------------------------------------------------------------------------------------------------
Total:16 Dynamic:10 Static:0 Interface:6
发现有两条ARP表项的“MAC ADDRESS”字段为“Incomplete”即为临时表项,表示有ARP表项学习不到。
3.3 判断设备正遭受ARP攻击。
a、由于有未学习到的ARP表项,查看上送CPU的ARP-Request报文统计信息。
<Switch_1>display cpu-defend arp-request statistics all
Statistics on mainboard:
------------------------------------------------------------------------------------------------------------------
Packet Type Pass(Bytes) Drop(Bytes) Pass(Packets) Drop(Packets)
-----------------------------------------------------------------------------------------------------------------
arp-request 67908288 0 1061067 0
------------------------------------------------------------------------------------------------------------------
Statistics on slot 4:
------------------------------------------------------------------------------------------------------------------
Packet Type Pass(Bytes) Drop(Bytes) Pass(Packets) Drop(Packets)
------------------------------------------------------------------------------------------------------------------
arp-request 80928 44380928 2301 693450
------------------------------------------------------------------------------------------------------------------
Statistics on slot 5:
------------------------------------------------------------------------------------------------------------------
Packet Type Pass(Bytes) Drop(Bytes) Pass(Packets) Drop(Packets)
------------------------------------------------------------------------------------------------------------------
arp-request N/A N/A 0 0
------------------------------------------------------------------------------------------------------------------
Statistics on slot 6:
------------------------------------------------------------------------------------------------------------------
Packet Type Pass(Bytes) Drop(Bytes) Pass(Packets) Drop(Packets)
------------------------------------------------------------------------------------------------------------------
arp-request N/A N/A 0 0
------------------------------------------------------------------------------------------------------------------
发现交换机的4号单板上存在大量ARP-Request报文丢包。
b、配置攻击溯源识别攻击源。
<Switch_1>system-view
[Switch_1]cpu-defend policy policy1
[Switch_1-cpu-defend-policy-policy1]auto-defend enable
[Switch_1-cpu-defend-policy-policy1]auto-defend attack-packet sample 5
//每5个报文抽样识别一次,抽样值过小会消耗过多CPU
[Switch_1-cpu-defend-policy-policy1]auto-defend threshold 30
//报文达30pps即被识别为攻击,若攻击源较多可调低该值
[Switch_1-cpu-defend-policy-policy1]undo auto-defend trace-type source-ip source-portvlan
//基于源MAC进行攻击源识别
[Switch_1-cpu-defend-policy-policy1]undo auto-defend protocol 8021x dhcp icmp igmp tcp telnet ttl-expired udp
//针对ARP攻击进行识别
[Switch_1-cpu-defend-policy-policy1]quit
[Switch_1]cpu-defend-policy policy1
[Switch_1]cpu-defend-policy policy1 global
c、查看攻击源信息。
[Switch_1]display auto-defend attack-source
Attack Source User Table (MPU):
------------------------------------------------------------------------------------------------
MacAddress InterfaceName Vlan:Outer/Inner TOTAL
------------------------------------------------------------------------------------------------
0000-0000-00db GigabitEthernet2/0/22 193 416
------------------------------------------------------------------------------------------------
发现攻击源的MAC地址为0000-0000-00db,位于GigabitEthernet2/0/22端口。
如果该MAC有对应ARP,还可以执行命令display arp | include 0000-0000-00db查询对应的IP。
四、解决方案
1、配置黑名单。
#
acl number 4000
rule 10 permit type 0806 ffff source-mac 0000-0000-00db ffff-ffff-ffff
#
cpu-defend policy 1
blacklist 1 acl 4000
//针对来自特定用户恶意报文的攻击,设备通过ACL把符合特定特征的用户纳入到黑名单中,被纳入黑名单的用户所发的报文到达设备后均会(公众号:网络工 程师阿 龙)被丢弃
#
cpu-defend-policy 1
cpu-defend-policy 1 global
#
2、配置攻击溯源的惩罚功能。
#
cpu-defend policy policy1
auto-defend enable
auto-defend threshold 30
undo auto-defend trace-type source-ip source-portvlan
undo auto-defend protocol 8021x dhcp icmp igmp tcp telnet ttl-expired udp
auto-defend action deny
//使能攻击溯源的惩罚功能,并指定惩罚措施。在默认惩罚时间300s内,将识别为攻击的报文全部丢弃
#
cpu-defend-policy policy1 global
cpu-defend-policy policy1
#