前言
是基于Client/Server的访问控制和认证协议。它可以限制未经授权的用户/设备通过接入端口(access port)访问LAN/WLAN。在获得交换机或LAN提供的各种业务之前,802.1x对连接到交换机端口上的用户/设备进行认证。在认证通过之前,802.1x只允许EAPOL(基于局域网的扩展认证协议)数据通过设备连接的交换机端口;认证通过以后,正常的数据可以顺利地通过以太网端口。
本文以公司内部员工接入WLAN网络使用802.1x认证方式为例介绍。
用户接入WLAN网络,使用802.1X客户端进行认证,输入正确的用户名和密码后可以无线上网。且在覆盖区域内移动发生漫游时,不影响用户的业务使用。
- AC组网方式:旁挂二层组网。
- DHCP部署方式:AC作为DHCP服务器为AP分配IP地址,SwitchB作为DHCP服务器为STA分配IP地址。
- 业务数据转发方式:直接转发。
- WLAN认证方式:WPA-WPA2+802.1X+AES。
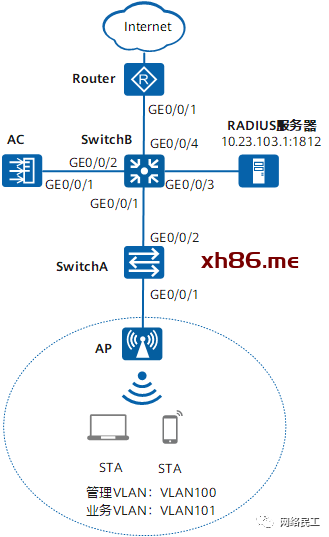
图1 配置802.1X认证组网图
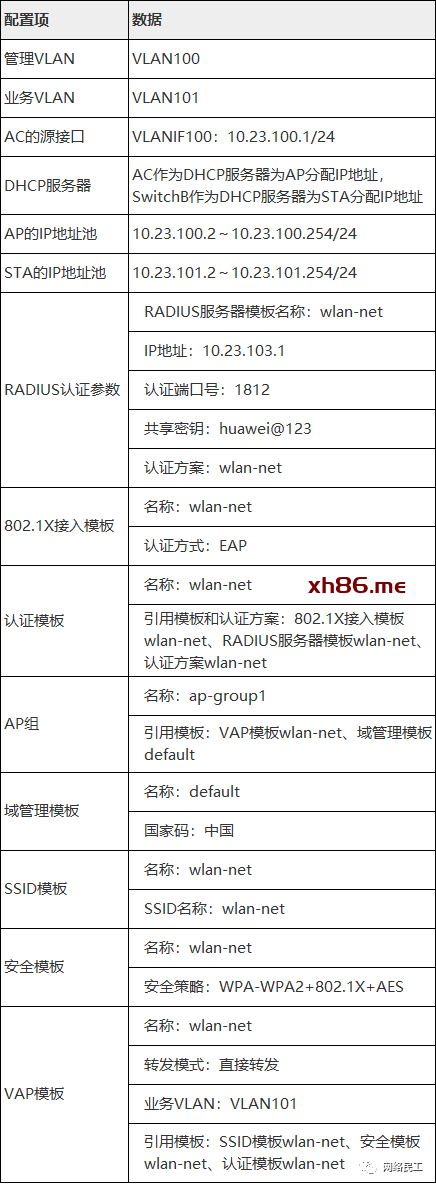
表1 AC数据规划表
【1】配置网络互通。
【2】配置AC和SwitchB分别给AP和STA分配IP地址。
【3】配置AP上线。
【4】配置AC上的802.1X认证。
【5】配置第三方服务器。
AC侧配置的RADIUS共享密钥需要和服务器侧保持一致。
配置注意事项
- 纯组播报文由于协议要求在无线空口没有ACK机制保障,且无线空口链路不稳定,为了纯组播报文能够稳定发送,通常会以低速报文形式发送。如果网络侧有大量异常组播流量涌入,则会造成无线空口拥堵。为了减小大量低速组播报文对无线网络造成的冲击,建议配置组播报文抑制功能。配置前请确认是否有组播业务,如果有,请谨慎配置限速值。
- 业务数据转发方式采用直接转发时,建议在直连AP的交换机接口上配置组播报文抑制。
- 业务数据转发方式采用隧道转发时,建议在AC的流量模板下配置组播报文抑制。
- 建议在与AP直连的设备接口上配置端口隔离,如果不配置端口隔离,尤其是业务数据转发方式采用直接转发时,可能会在VLAN内形成大量不必要的广播报文,导致网络阻塞,影响用户体验。
- 隧道转发模式下,管理VLAN和业务VLAN不能配置为同一VLAN,且AP和AC之间只能放通管理VLAN,不能放通业务VLAN。
- 802.1X认证场景下,由于EAP报文属于控制报文需要通过CAPWAP隧道到AC,所以不管直接转发还是隧道转发,都需要保证AC上创建相应的业务VLAN。
【1】配置网络互通
# 配置接入交换机SwitchA的接口GE0/0/1和GE0/0/2加入VLAN100和VLAN101。
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 100 101 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk pvid vlan 100 [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 101 [SwitchA-GigabitEthernet0/0/1] port-isolate enable [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type trunk [SwitchA-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 101 [SwitchA-GigabitEthernet0/0/2] quit
# 配置汇聚交换机SwitchB的接口GE0/0/1加入VLAN100和VLAN101,GE0/0/2加入VLAN100和VLAN102,GE0/0/3加入VLAN103,GE0/0/4加入VLAN104,创建VLANIF102、VLANIF103和VLANIF104接口,并配置下一跳为Router的缺省路由。
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan batch 100 to 104 [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type trunk [SwitchB-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 101 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface gigabitethernet 0/0/2 [SwitchB-GigabitEthernet0/0/2] port link-type trunk [SwitchB-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 102 [SwitchB-GigabitEthernet0/0/2] quit [SwitchB] interface gigabitethernet 0/0/3 [SwitchB-GigabitEthernet0/0/3] port link-type trunk [SwitchB-GigabitEthernet0/0/3] port trunk pvid vlan 103 [SwitchB-GigabitEthernet0/0/3] port trunk allow-pass vlan 103 [SwitchB-GigabitEthernet0/0/3] quit [SwitchB] interface gigabitethernet 0/0/4 [SwitchB-GigabitEthernet0/0/4] port link-type trunk [SwitchB-GigabitEthernet0/0/4] port trunk pvid vlan 104 [SwitchB-GigabitEthernet0/0/4] port trunk allow-pass vlan 104 [SwitchB-GigabitEthernet0/0/4] quit [SwitchB] interface vlanif 102 [SwitchB-Vlanif102] ip address 10.23.102.1 24 [SwitchB-Vlanif102] quit [SwitchB] interface vlanif 103 [SwitchB-Vlanif103] ip address 10.23.103.2 24 [SwitchB-Vlanif103] quit [SwitchB] interface vlanif 104 [SwitchB-Vlanif104] ip address 10.23.104.1 24 [SwitchB-Vlanif104] quit [SwitchB] ip route-static 0.0.0.0 0.0.0.0 10.23.104.2
# 配置AC的接口GE0/0/1加入VLAN100和VLAN102,创建VLANIF102接口,并配置指向RADIUS服务器的静态路由。
<AC6605> system-view [AC6605] sysname AC [AC] vlan batch 100 101 102 [AC] interface gigabitethernet 0/0/1 [AC-GigabitEthernet0/0/1] port link-type trunk [AC-GigabitEthernet0/0/1] port trunk allow-pass vlan 100 102 [AC-GigabitEthernet0/0/1] quit [AC] interface vlanif 102 [AC-Vlanif102] ip address 10.23.102.2 24 [AC-Vlanif102] quit [AC] ip route-static 10.23.103.0 24 10.23.102.1
# 配置Router的接口GE0/0/1的IP地址,并配置指向STA网段的静态路由。
<Huawei> system-view [Huawei] sysname Router [Router] interface gigabitethernet 0/0/1 [Router-GigabitEthernet0/0/1] ip address 10.23.104.2 24 [Router-GigabitEthernet0/0/1] quit [Router] ip route-static 10.23.101.0 24 10.23.104.1
【2】配置AC作为DHCP服务器为AP分配IP地址,SwitchB作为DHCP服务器为STA分配IP地址
# 在AC上配置VLANIF100接口为AP提供IP地址。
[AC] dhcp enable [AC] interface vlanif 100 [AC-Vlanif100] ip address 10.23.100.1 24 [AC-Vlanif100] dhcp select interface [AC-Vlanif100] quit
# 在SwitchB上配置VLANIF101接口为STA提供IP地址。
[SwitchB] dhcp enable [SwitchB] interface vlanif 101 [SwitchB-Vlanif101] ip address 10.23.101.1 24 [SwitchB-Vlanif101] dhcp select interface [SwitchB-Vlanif101] quit
【3】配置AP上线
# 创建AP组,用于将相同配置的AP都加入同一AP组中。
[AC] wlan [AC-wlan-view] ap-group name ap-group1 [AC-wlan-ap-group-ap-group1] quit
# 创建域管理模板,在域管理模板下配置AC的国家码并在AP组下引用域管理模板。
[AC-wlan-view] regulatory-domain-profile name default [AC-wlan-regulate-domain-default] country-code cn [AC-wlan-regulate-domain-default] quit [AC-wlan-view] ap-group name ap-group1 [AC-wlan-ap-group-ap-group1] regulatory-domain-profile default Warning: Modifying the country code will clear channel, power and antenna gain configurations of the radio and reset the AP. Continu e?[Y/N]:y [AC-wlan-ap-group-ap-group1] quit [AC-wlan-view] quit
# 配置AC的源接口。
[AC] capwap source interface vlanif 100
# 在AC上离线导入AP,并将AP加入AP组“ap-group1”中。假设AP的MAC地址为60de-4476-e360,并且根据AP的部署位置为AP配置名称,便于从名称上就能够了解AP的部署位置。例如MAC地址为60de-4476-e360的AP部署在1号区域,命名此AP为area_1。
[AC] wlan
[AC-wlan-view] ap auth-mode mac-auth
[AC-wlan-view] ap-id 0 ap-mac 60de-4476-e360
[AC-wlan-ap-0] ap-name area_1
[AC-wlan-ap-0] ap-group ap-group1
Warning: This operation may cause AP reset. If the country code changes, it will clear channel, power and antenna gain configuration
s of the radio, Whether to continue? [Y/N]:y
[AC-wlan-ap-0] quit
# 将AP上电后,当执行命令display ap all查看到AP的“State”字段为“nor”时,表示AP正常上线。
[AC-wlan-view] display ap all
Total AP information:
nor : normal [1]
-------------------------------------------------------------------------------------------------
ID MAC Name Group IP Type State STA Uptime ExtraInfo
-------------------------------------------------------------------------------------------------
0 60de-4476-e360 area_1 ap-group1 10.23.100.254 AP5030DN nor 0 10S -
-------------------------------------------------------------------------------------------------
Total: 1
【4】配置AP射频的信道和功率
射频的信道和功率自动调优功能默认开启,如果不关闭此功能则会导致手动配置不生效。举例中AP射频的信道和功率仅为示例,实际配置中请根据AP的国家码和网规结果进行配置。
# 关闭AP射频0的信道和功率自动调优功能,并配置AP射频0的信道和功率。
[AC-wlan-view] ap-id 0
[AC-wlan-ap-0] radio 0
[AC-wlan-radio-0/0] calibrate auto-channel-select disable
[AC-wlan-radio-0/0] calibrate auto-txpower-select disable
[AC-wlan-radio-0/0] channel 20mhz 6
Warning: This action may cause service interruption. Continue?[Y/N]y
[AC-wlan-radio-0/0] eirp 127
[AC-wlan-radio-0/0] quit
# 关闭AP射频1的信道和功率自动调优功能,并配置AP射频1的信道和功率。
[AC-wlan-ap-0] radio 1
[AC-wlan-radio-0/1] calibrate auto-channel-select disable
[AC-wlan-radio-0/1] calibrate auto-txpower-select disable
[AC-wlan-radio-0/1] channel 20mhz 149
Warning: This action may cause service interruption. Continue?[Y/N]y
[AC-wlan-radio-0/1] eirp 127
[AC-wlan-radio-0/1] quit
[AC-wlan-ap-0] quit
【5】在AC上配置802.1X认证
A、配置RADIUS认证参数。
# 创建RADIUS服务器模板。
[AC-wlan-view] quit [AC] radius-server template wlan-net [AC-radius-wlan-net] radius-server authentication 10.23.103.1 1812 [AC-radius-wlan-net] radius-server shared-key cipher huawei@123 [AC-radius-wlan-net] quit
# 创建RADIUS方式的认证方案。
[AC] aaa [AC-aaa] authentication-scheme wlan-net [AC-aaa-authen-wlan-net] authentication-mode radius [AC-aaa-authen-wlan-net] quit [AC-aaa] quit
B、配置802.1X接入模板,管理802.1X接入控制参数。
# 创建名为“wlan-net”的802.1X接入模板。
[AC] dot1x-access-profile name wlan-net
# 配置认证方式为EAP中继模式。
[AC-dot1x-access-profile-wlan-net] dot1x authentication-method eap [AC-dot1x-access-profile-wlan-net] quit
C、创建名为“wlan-net”的认证模板,并引用802.1X接入模板、认证方案和RADIUS服务器模板。
[AC] authentication-profile name wlan-net [AC-authentication-profile-wlan-net] dot1x-access-profile wlan-net [AC-authentication-profile-wlan-net] authentication-scheme wlan-net [AC-authentication-profile-wlan-net] radius-server wlan-net [AC-authentication-profile-wlan-net] quit
D、配置WLAN业务参数。
# 创建名为“wlan-net”的安全模板,并配置安全策略。
[AC] wlan [AC-wlan-view] security-profile name wlan-net [AC-wlan-sec-prof-wlan-net] security wpa-wpa2 dot1x aes [AC-wlan-sec-prof-wlan-net] quit
# 创建名为“wlan-net”的SSID模板,并配置SSID名称为“wlan-net”。
[AC-wlan-view] ssid-profile name wlan-net [AC-wlan-ssid-prof-wlan-net] ssid wlan-net [AC-wlan-ssid-prof-wlan-net] quit
# 创建名为“wlan-net”的VAP模板,配置业务数据转发模式为直接转发、业务VLAN,并且引用安全模板、认证模板和SSID模板。
[AC-wlan-view] vap-profile name wlan-net [AC-wlan-vap-prof-wlan-net] forward-mode direct-forward [AC-wlan-vap-prof-wlan-net] service-vlan vlan-id 101 [AC-wlan-vap-prof-wlan-net] security-profile wlan-net [AC-wlan-vap-prof-wlan-net] authentication-profile wlan-net [AC-wlan-vap-prof-wlan-net] ssid-profile wlan-net [AC-wlan-vap-prof-wlan-net] quit
# 配置AP组引用VAP模板,AP上射频0和射频1都使用VAP模板“wlan-net”的配置。
[AC-wlan-view] ap-group name ap-group1 [AC-wlan-ap-group-ap-group1] vap-profile wlan-net wlan 1 radio 0 [AC-wlan-ap-group-ap-group1] vap-profile wlan-net wlan 1 radio 1 [AC-wlan-ap-group-ap-group1] quit [AC-wlan-view] quit
【6】配置第三方服务器
具体配置方法略
【7】检查配置结果
完成配置后,用户可通过无线终端搜索到SSID为wlan-net的无线网络。
用户关联到无线网络上后,无线PC能够被分配相应的IP地址。
在STA上使用802.1X客户端进行认证,输入正确的用户名和密码后,STA认证成功,正常访问WLAN网络。需要根据设置的认证方式PEAP对客户端进行相应的配置。
这里以Windows 7系统下的配置为例:
- 进入管理无线网络页面,单击“添加”,选择手动创建网络配置文件,添加SSID为wlan-net,并选择认证方式为WPA2-企业,加密使用的算法AES,单击“下一步”。
- 单击“更改连接设置”,进入“无线网络属性”界面,选择“安全”页签,单击“设置”,取消勾选“验证服务器证书”(此处不验证服务器证书),单击“配置”,取消勾选“自动使用Windows登录名和密码”,单击“确定”。
- 单击“确定”,返回“无线网络属性”界面,单击“高级设置”,在“高级设置”界面,勾选“指定身份验证模式”,并选择身份验证模式为“用户身份验证”,单击“确定”。
无线用户接入后,在AC上执行命令display access-user access-type dot1x,可以查看到认证类型为“802.1X”的用户中,名为“huawei”的用户已成功上线。
[AC] display access-user access-type dot1x ------------------------------------------------------------------------------ UserID Username IP address MAC Status ------------------------------------------------------------------------------ 460 huawei 10.23.101.254 8000-6e74-e78a Success ------------------------------------------------------------------------------ Total: 1, printed: 1
SwitchA的配置文件
sysname SwitchA # vlan batch 100 to 101 # interface GigabitEthernet0/0/1 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 to 101 port-isolate enable group 1 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 to 101
SwitchB的配置文件
sysname SwitchB # vlan batch 100 to 104 # dhcp enable # interface Vlanif101 ip address 10.23.101.1 255.255.255.0 dhcp select interface # interface Vlanif102 ip address 10.23.102.1 255.255.255.0 # interface Vlanif103 ip address 10.23.103.2 255.255.255.0 # interface Vlanif104 ip address 10.23.104.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 to 101 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 102 # interface GigabitEthernet0/0/3 port link-type trunk port trunk pvid vlan 103 port trunk allow-pass vlan 103 # interface GigabitEthernet0/0/4 port link-type trunk port trunk pvid vlan 104 port trunk allow-pass vlan 104 # ip route-static 0.0.0.0 0.0.0.0 10.23.104.2
Router的配置文件
sysname Router # interface GigabitEthernet0/0/1 ip address 10.23.104.2 255.255.255.0 # ip route-static 10.23.101.0 255.255.255.0 10.23.104.1
AC的配置文件
sysname AC # vlan batch 100 to 102 # authentication-profile name wlan-net dot1x-access-profile wlan-net authentication-scheme wlan-net radius-server wlan-net # dhcp enable # radius-server template wlan-net radius-server shared-key cipher %^%#*7d1;XNof/|Q0:DsP!,W51DIYPx}`AARBdJ'0B^$%^%# radius-server authentication 10.23.103.1 1812 weight 80 # aaa authentication-scheme wlan-net authentication-mode radius # interface Vlanif100 ip address 10.23.100.1 255.255.255.0 dhcp select interface # interface Vlanif102 ip address 10.23.102.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 102 # ip route-static 10.23.103.0 255.255.255.0 10.23.102.1 # capwap source interface vlanif100 # wlan security-profile name wlan-net security wpa-wpa2 dot1x aes ssid-profile name wlan-net ssid wlan-net vap-profile name wlan-net service-vlan vlan-id 101 ssid-profile wlan-net security-profile wlan-net authentication-profile wlan-net regulatory-domain-profile name default ap-group name ap-group1 radio 0 vap-profile wlan-net wlan 1 radio 1 vap-profile wlan-net wlan 1 ap-id 0 type-id 35 ap-mac 60de-4476-e360 ap-sn 210235554710CB000042 ap-name area_1 ap-group ap-group1 radio 0 channel 20mhz 6 eirp 127 calibrate auto-channel-select disable calibrate auto-txpower-select disable radio 1 channel 20mhz 149 eirp 127 calibrate auto-channel-select disable calibrate auto-txpower-select disable # dot1x-access-profile name wlan-net